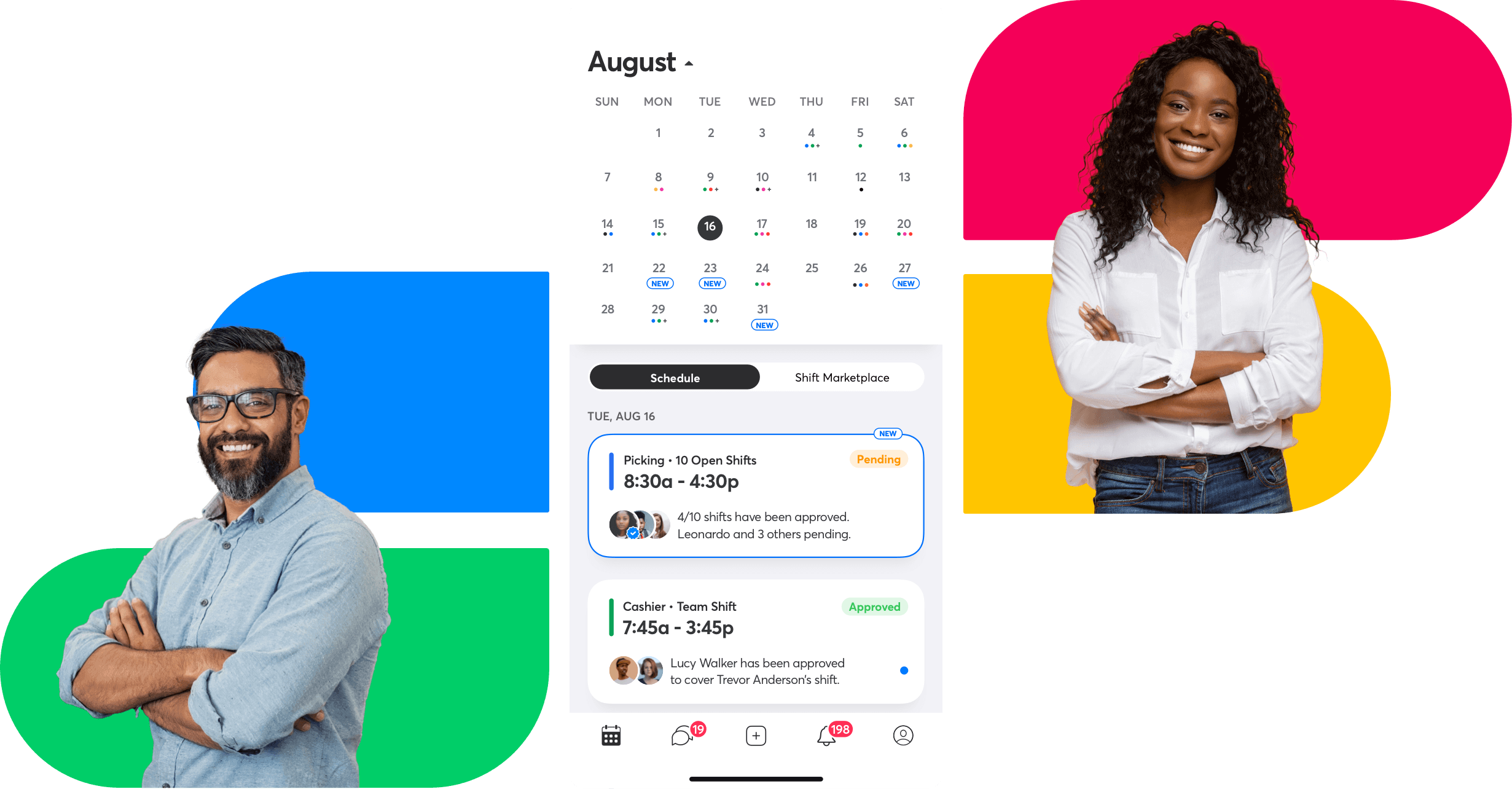
In today’s dynamic workplace environment, managing who can view and edit appointment details is crucial for organizational security and operational efficiency. Granular access controls for appointment details within Shyft’s platform offer businesses the ability to precisely manage which team members can access specific scheduling information, protecting sensitive data while ensuring seamless operations. These sophisticated permission settings allow organizations to establish secure boundaries around appointment data, striking the perfect balance between information sharing and data protection.
Businesses across industries—from retail and healthcare to hospitality and supply chain—increasingly recognize that one-size-fits-all access policies create either security vulnerabilities or workflow bottlenecks. The implementation of granular access controls addresses these challenges by tailoring visibility and edit permissions to specific roles, responsibilities, and organizational hierarchies. With Shyft’s comprehensive access control mechanisms, companies can customize data access down to the individual appointment level, creating a secure yet efficient scheduling ecosystem.
Understanding the Fundamentals of Access Control in Scheduling Systems
Access control mechanisms in scheduling software serve as the foundation for maintaining data security while enabling productivity. At their core, these systems determine which users can view, edit, or manage different types of appointment information based on predefined permissions. Shyft’s advanced features approach access control through a layered framework that balances security with usability, allowing organizations to create permission structures that align with their operational needs.
- Role-based Access Control (RBAC): Permissions assigned based on job functions, ensuring managers, team leads, and frontline employees see only what’s relevant to their responsibilities.
- Attribute-based Access Control (ABAC): Access determined by specific attributes of appointments, users, or environmental conditions like time or location.
- Hierarchical Access Models: Tiered permission structures that mirror organizational reporting lines and supervisory relationships.
- Context-aware Permissions: Dynamic access rules that adapt based on factors like shift timing, emergency status, or business conditions.
- Multi-factor Authentication: Additional security layers for accessing highly sensitive appointment details.
Understanding these fundamental models is essential for organizations implementing access control mechanisms in their scheduling environment. According to research by the Ponemon Institute, 63% of data breaches involve access privilege issues, highlighting the critical importance of properly configured access controls.
Types of Granular Access Controls in Shyft
Shyft’s platform offers a sophisticated array of granular access control options, allowing organizations to customize permissions at multiple levels. These controls can be configured to meet specific business requirements while maintaining data privacy and operational efficiency. The flexibility of Shyft’s access control system makes it adaptable to organizations of all sizes and across diverse industries.
- Department-level Controls: Restrict appointment visibility to specific departments or functional teams, preventing cross-departmental data exposure.
- Location-based Permissions: Limit access to appointment data based on physical location or store/facility designations.
- Time-bounded Access: Grant temporary access to appointment details for specific periods, perfect for covering managers or temporary staff.
- Field-level Restrictions: Control which specific appointment data fields (customer information, service details, notes) are visible to different user types.
- Action-based Permissions: Separate view, edit, delete, and management capabilities for fine-tuned control over user actions.
As noted in Shyft’s data privacy practices, these granular controls allow businesses to maintain compliance with regulations like GDPR and HIPAA while optimizing workflows. Organizations leveraging Shyft’s employee scheduling systems can implement these controls to protect sensitive customer and employee information.
Benefits of Implementing Granular Access Controls for Appointment Details
Deploying granular access controls for appointment details delivers substantial benefits that extend beyond simple security improvements. Organizations that implement these sophisticated permission structures experience advantages in multiple operational areas, creating a stronger foundation for sustainable business growth and efficient workforce management.
- Enhanced Data Security: Minimize the risk of unauthorized access to sensitive appointment information, protecting both customer and business data.
- Regulatory Compliance: Meet legal requirements for data protection and privacy across various jurisdictions and industries.
- Streamlined Operations: Reduce information overload by showing employees only the appointment details relevant to their roles.
- Reduced Error Risk: Prevent accidental changes to appointments by limiting edit capabilities to authorized personnel.
- Improved Accountability: Track and audit appointment changes with clear user attribution for all system actions.
Research highlighted in Shyft’s security features documentation shows that businesses implementing granular access controls report up to 47% fewer scheduling errors and a 38% improvement in compliance outcomes. These controls work seamlessly with Shyft’s team communication features to ensure information flows appropriately throughout the organization.
Configuring Access Controls for Different User Roles
Effective implementation of granular access controls requires thoughtful configuration based on organizational structure and user responsibilities. Shyft’s platform makes this process intuitive through role-based permission templates that can be customized to match specific business requirements. By aligning access privileges with job functions, companies create a more secure and efficient scheduling environment.
- Executive-level Access: Comprehensive visibility across all departments with reporting capabilities but typically limited direct editing privileges.
- Manager Permissions: Full access to appointments within their domain, including scheduling, editing, and approval capabilities.
- Supervisor Controls: Team-specific appointment visibility with the ability to make adjustments within defined parameters.
- Employee Access: View-only access to personal schedules and limited team information, with self-service options for requests.
- Administrative Roles: Specialized access focused on system configuration rather than appointment content.
As detailed in Shyft’s HR management systems integration documentation, these role configurations can be synchronized with existing HR systems to maintain consistency across organizational tools. This approach supports strategic workforce planning by ensuring the right people have appropriate access to scheduling information.
Security Considerations for Protecting Appointment Data
Beyond basic access controls, protecting appointment data requires a comprehensive security approach that addresses multiple vulnerabilities and threat vectors. Shyft’s platform incorporates advanced security measures that work in concert with access controls to create multiple layers of protection. These safeguards ensure that sensitive appointment details remain confidential while still being available to authorized users when needed.
- End-to-end Encryption: All appointment data encrypted both in transit and at rest to prevent unauthorized interception.
- Audit Logging: Comprehensive tracking of all user interactions with appointment data for accountability and compliance.
- Session Management: Automatic timeouts and secure login requirements to prevent unauthorized access from unattended devices.
- Data Masking: Concealing sensitive portions of appointment details based on user access levels.
- Secure API Access: Protected integration points when connecting with other business systems.
According to Shyft’s security documentation, implementing these protective measures alongside granular access controls creates a defense-in-depth strategy that significantly reduces security risks. Organizations in regulated industries like healthcare particularly benefit from these robust security features when managing sensitive appointment information.
Integrating Access Controls with Other Shyft Features
The power of Shyft’s granular access controls is magnified when integrated with other platform features, creating a cohesive ecosystem that balances security with functionality. These integrations enable businesses to maintain strict access controls while still leveraging the full capabilities of the scheduling platform. The seamless connections between different Shyft modules ensure that permission settings are consistently applied across all user interactions.
- Shift Marketplace Integration: Access controls determine which employees can view and claim open shifts while protecting shift details.
- Communication Tool Synchronization: Permissions automatically align with messaging capabilities to prevent unauthorized information sharing.
- Reporting Engine Alignment: Access levels determine which metrics and analytics are available to different user types.
- Mobile App Security: Consistent permission enforcement across both desktop and mobile interfaces.
- Notification System Controls: Personalized alerts based on access rights and responsibilities.
As highlighted in Shyft’s integration capabilities overview, these interconnected features create a secure yet fluid scheduling environment. Organizations using Shyft’s shift marketplace find that appropriate access controls enhance rather than hinder the flexibility of their scheduling systems.
Industry-Specific Applications of Granular Access Controls
Different industries have unique requirements for appointment data protection, and Shyft’s granular access controls can be tailored to address these specific needs. From sensitive patient information in healthcare to high-value customer appointments in financial services, customized access controls ensure appropriate protection while enabling necessary workflow functions. These industry-specific applications demonstrate the versatility of Shyft’s access control mechanisms.
- Healthcare Settings: HIPAA-compliant access controls that protect patient information while enabling clinical team coordination.
- Retail Environments: Department-specific permissions that manage specialized service appointments and customer information.
- Hospitality Industry: Location-based controls that manage appointment details across multiple properties or service areas.
- Supply Chain Operations: Time-sensitive access controls for delivery appointments and logistics scheduling.
- Financial Services: Strict hierarchical permissions for high-value client meetings and consultations.
As described in Shyft’s industry compliance documentation, these specialized configurations ensure businesses meet regulatory requirements while maintaining operational efficiency. Companies in sectors like retail and hospitality can implement industry-specific templates to accelerate their security configuration process.
Implementation Best Practices for Access Control Mechanisms
Successfully implementing granular access controls requires careful planning and strategic execution. Organizations that follow established best practices experience smoother deployments with higher user acceptance and stronger security outcomes. These methodologies help businesses avoid common pitfalls while maximizing the effectiveness of their access control systems.
- Conduct Access Needs Assessment: Systematically analyze which roles need what level of appointment information access before configuration.
- Apply Least Privilege Principle: Grant the minimum necessary access required for each role to perform its functions.
- Document Access Policies: Create clear, comprehensive documentation of all access rules and justifications.
- Implement Gradual Rollout: Phase in access controls starting with less sensitive areas to allow for adjustment.
- Conduct Regular Access Reviews: Schedule periodic audits of access privileges to identify and correct permission drift.
Shyft’s implementation guidance provides detailed roadmaps for organizations deploying access control systems. Research cited in Shyft’s system performance evaluations indicates that businesses following these best practices achieve 76% faster user adoption and 82% fewer security incidents in the first year after implementation.
Advanced Features of Shyft’s Access Control Mechanisms
Beyond standard permission settings, Shyft offers advanced access control capabilities that provide unprecedented flexibility and security for managing appointment details. These sophisticated features allow organizations to create highly customized security environments that adapt to changing business conditions while maintaining strict protection of sensitive information. These cutting-edge controls represent the latest innovations in scheduling system security.
- Contextual Access Rules: Dynamic permissions that change based on factors like time of day, device type, or network location.
- Temporary Access Elevation: Just-in-time permission increases for specific tasks with automatic reversion afterward.
- AI-Powered Anomaly Detection: Machine learning algorithms that identify unusual access patterns and potential security risks.
- Delegated Administration: Distributed security management that allows department heads to manage access within their domains.
- Custom Approval Workflows: Multi-step verification processes for accessing highly sensitive appointment details.
As detailed in Shyft’s AI and machine learning documentation, these advanced features represent the cutting edge of scheduling security. Organizations looking to maximize protection while maintaining flexibility can leverage these capabilities as described in Shyft’s advanced feature guides.
Future Trends in Access Control for Scheduling Software
The landscape of appointment security and access control continues to evolve rapidly, with emerging technologies and changing business needs driving innovation. Understanding these trends helps organizations prepare for future developments and make strategic decisions about their access control implementations. Shyft remains at the forefront of these advancements, continuously enhancing its security capabilities to address evolving challenges.
- Biometric Authentication Integration: Fingerprint, facial recognition, and other biometric factors for accessing sensitive appointment details.
- Zero-Trust Architecture: Security models that require verification for every access request regardless of source or location.
- Blockchain for Access Logging: Immutable records of all permission changes and access events for perfect accountability.
- Predictive Access Models: AI systems that anticipate access needs and proactively adjust permissions.
- Natural Language Processing for Permissions: Voice-controlled access management for hands-free security administration.
These emerging technologies align with trends discussed in Shyft’s future trends analysis. Organizations preparing for long-term success should consider how these developments might impact their data privacy approaches and scheduling security strategies.
Conclusion: Maximizing Security and Efficiency with Granular Access Controls
Granular access controls for appointment details represent a critical component of modern scheduling systems, balancing the essential requirements of data security with operational efficiency. By implementing Shyft’s sophisticated access control mechanisms, organizations can protect sensitive information while enabling smooth workflows that drive productivity. The ability to precisely define who can view, edit, and manage different aspects of appointment data creates a secure foundation for all scheduling activities.
As businesses continue to navigate complex regulatory environments and evolving security threats, investing in robust access control systems becomes increasingly important. Shyft’s comprehensive approach to appointment security offers the flexibility, customization, and advanced protection features that organizations need to meet these challenges. By following implementation best practices and leveraging industry-specific configurations, companies across sectors can establish access control frameworks that enhance both security and operational performance, creating lasting value for their scheduling ecosystems and stakeholder relationships.
FAQ
1. What are granular access controls for appointment details in Shyft?
Granular access controls in Shyft are sophisticated permission settings that allow organizations to precisely define which users can view, edit, delete, or manage different aspects of appointment information. These controls can be configured based on roles, departments, locations, time periods, and other attributes, creating a highly customized security environment that protects sensitive data while enabling necessary workflow functions.
2. How do granular access controls help with regulatory compliance?
Granular access controls are essential for regulatory compliance across multiple frameworks including GDPR, HIPAA, and industry-specific regulations. They help organizations implement data minimization principles by ensuring users only access information necessary for their roles, maintain audit trails of all data interactions, enforce data access policies consistently, and demonstrate due diligence in protecting sensitive information. These capabilities are crucial for passing compliance audits and avoiding potential penalties.
3. Can access controls be configured differently for various departments?
Yes, Shyft’s access control system is designed to support department-specific configurations that reflect different operational needs. Organizations can create unique permission profiles for each department that specify which appointment details are visible and editable. For example, the HR department might have access to employee-related appointment data while being restricted from customer appointment details, and retail floor managers might only see appointments for their specific department or location.
4. What security measures complement granular access controls in Shyft?
Shyft employs multiple security layers that work alongside access controls including end-to-end encryption of all appointment data, comprehensive audit logging of system activities, secure authentication mechanisms including multi-factor options, automatic session timeouts to prevent unauthorized access, data masking for sensitive information, and regular security updates to address emerging threats. This defense-in-depth approach ensures that appointment details remain protected even if a single security control is compromised.
5. How can organizations determine the right level of access control granularity?
Finding the optimal balance for access control granularity requires organizations to assess several factors: regulatory requirements for their industry, sensitivity of the appointment data being managed, operational efficiency needs, organizational structure and reporting relationships, and specific security risks. Shyft recommends starting with a detailed access needs assessment, implementing controls based on the principle of least privilege, and then refining permission settings based on user feedback and operational metrics. Regular security reviews should be conducted to ensure the granularity level remains appropriate as the organization evolves.